In this exploit the payload, or certain characters in the payload, are transformed in a way that changes the value when the payload is used by the application. Transformation occurs when the application encodes or decodes your payload/part of your payload, makes characters upper or lower case, etc.
The WAF is usually unaware of transformations because they occur within the application. This means that, if we can adapt a payload to the transformation the application will perform, we can then bypass the WAF because our “invalid” payload will then be seen in its expected form once the application performs the transformation.
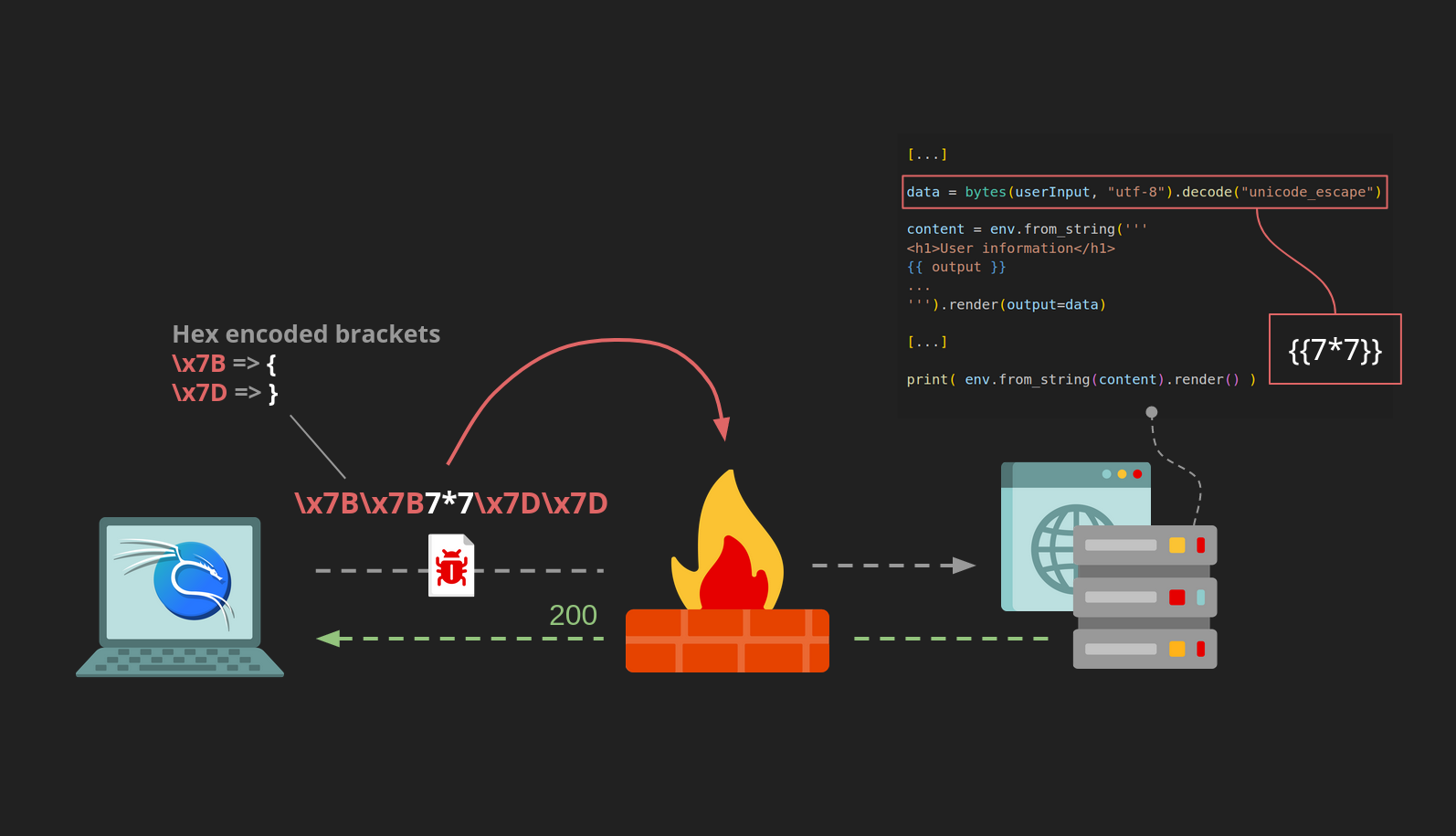
You can see an example of this exploit in the image below. The attacker sends the template injection payload: \x7B\x7B7*7\x7D\x7D. This is then transformed to: {{7*7}} by the vulnerable application. In the video below you can watch Brumens' presentation on bypassing WAFs at Nahamcon 2024, where he explains the technique in detail and walks attendees through the related lab linked at the bottom of this page.
In the video below you can find the presentation from Brumens that was part of Nahamcon 2024 where he explains the technique in detail and also goes through the lab linked at the bottom of this page.
Now that you know how transformations work, you can test your practical skills in the lab below.