A filter collision occurs when the vulnerable application uses a filter that transforms the payload (usually by removing parts of the payload). This flaw in the filter's behaviour can then be exploited to bypass the WAF.
Imagine a scenario as shown in the image below:
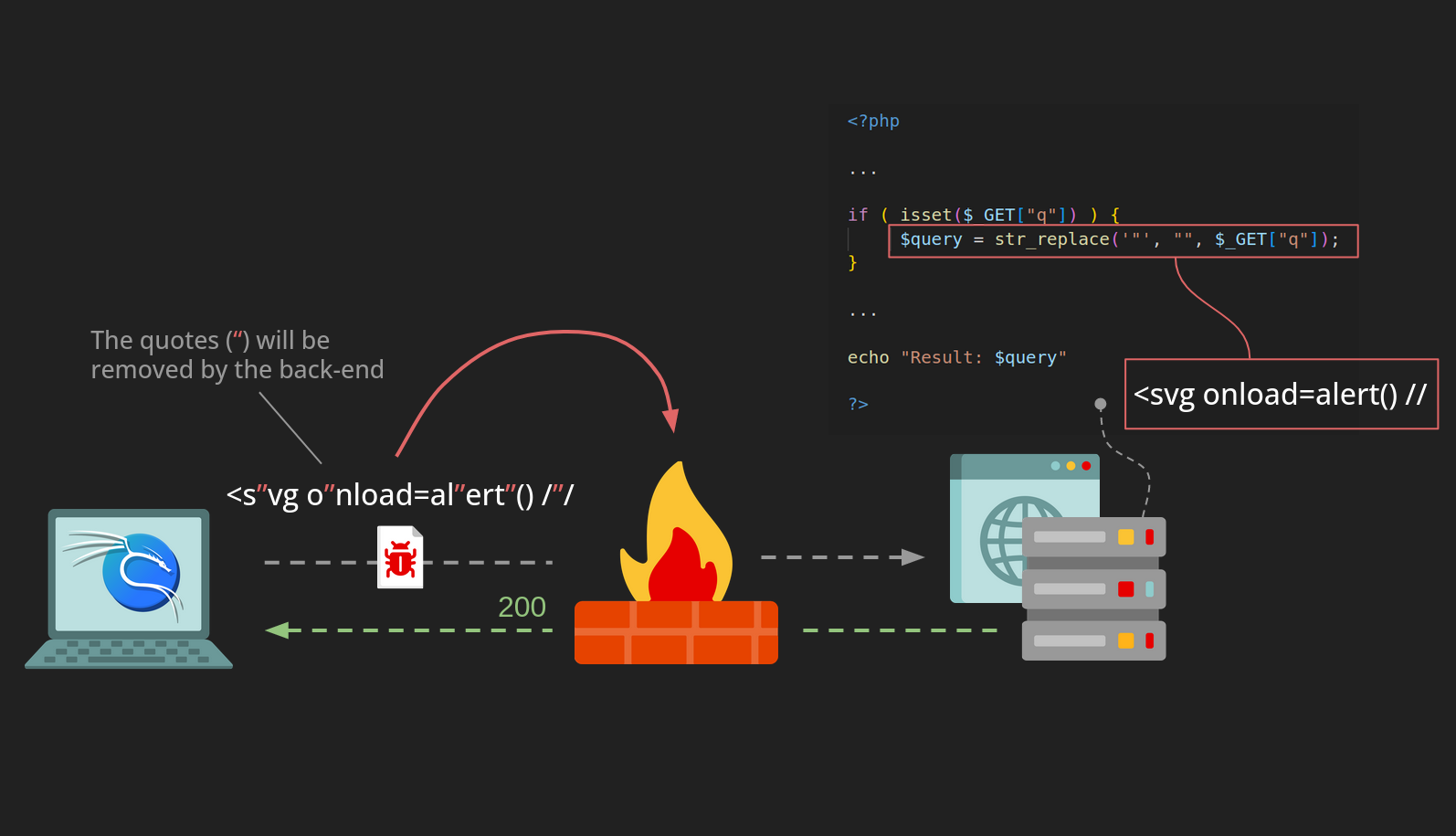
The vulnerable application removes double quotes (") from the payload sent by the client. This is then reflected back to us in the response. We can take advantage of this by creating a payload containing randomly inserted double quotes, which will ensure the WAF cannot detect malicious keywords or regex patterns in our payload.
An application should never remove characters from a payload unless it replaces them with other characters. If you remove a character from a malicious payload, any protective mechanism that analysed the payload before your modification will subsequently be unable to detect that the payload is malicious. This is because a different version of the original payload is created when it hits the backend filter.
In the video below you can watch Brumens' presentation: "The Art of Bypassing WAF's" at Nahamcon 2024, where he explains the technique in detail and walks attendees through the related lab linked at the bottom of this page.
Now that you know how a filter collision works, you can test your practical skills in the lab below.