Python's function yaml.load is used to deserialise data into YAML. However, if the YAML data being deserialised is user-controllable and the YAML loader on the application uses the default YAML loader, it is possible for an attacker to execute Python code during the YAML deserialisation process.
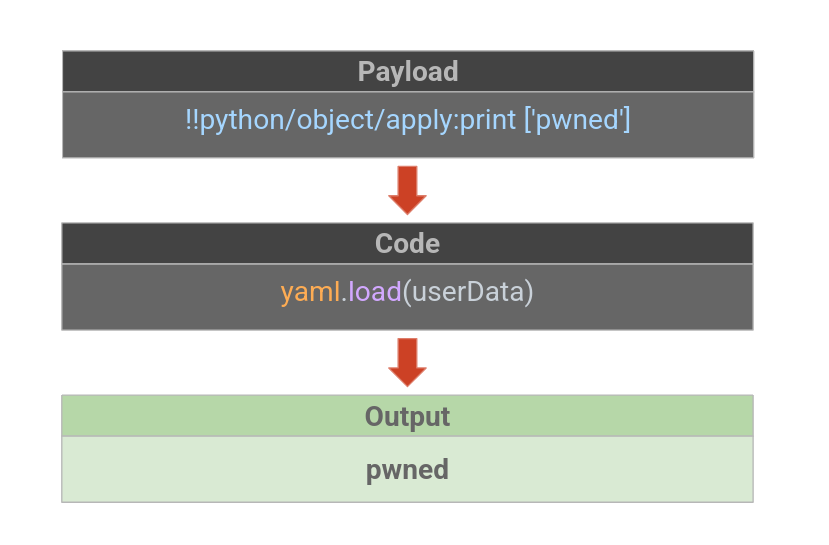
Example of vulnerable code: An attacker can exploit the yaml.load function by adding the YAML code: !!python/object/apply:print ['pwned'] at the beginning of the YAML data. This tells the YAML load function to execute the Python code: print('pwned') and allow an attacker to exploit a code injection (CWE-94) vulnerability.
The attack workflow can be illustratied as shown below:

Now that you know how you can use this techniques to your advantage, you can test your practical skills in the official lab below.