Python Pitfalls - pickle
Python's function pickle.loads is used to deserialise a Python object structure. However, if the data being deserialised can be controlled by the user, it is possible for an attacker to perform a code injection and compromise the vulnerable application.
Example of vulnerable code: An attacker can exploit pickle.loads by creating a Python script that generates a serialised payload that executes system commands on the vulnerable target. The Python script might look something like this:
You can try the pickle exploit script here
To summarise, the attack workflow can be illustrated as follows:
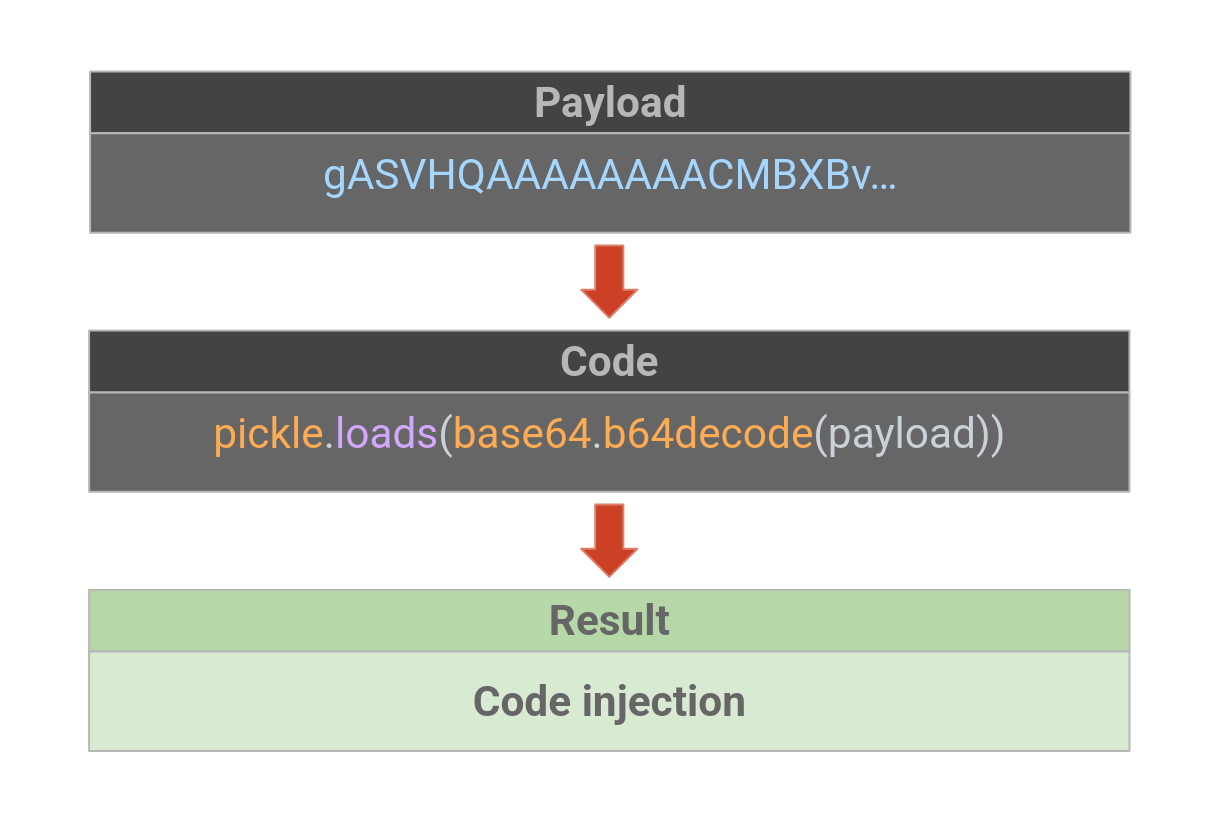
Now that you know how you can use this techniques to your advantage, you can test your practical skills in the official lab below.