Similar to Prototype Pollution in JavaScript, Python can be exposed to a class pollution vulnerability when untrusted input modifies class-level attributes instead of instance-level data. Because Python classes are mutable, a single write to the class affects all existing and future instances that depend on that attribute. If an attacker can influence a function such as setattr, a deserialised object, or any logic that writes directly to a class, they can reshape the global behaviour.
An attacker can use the following attack technique and payload to overwrite the variable CHANGEME with a new value specified by the attacker.
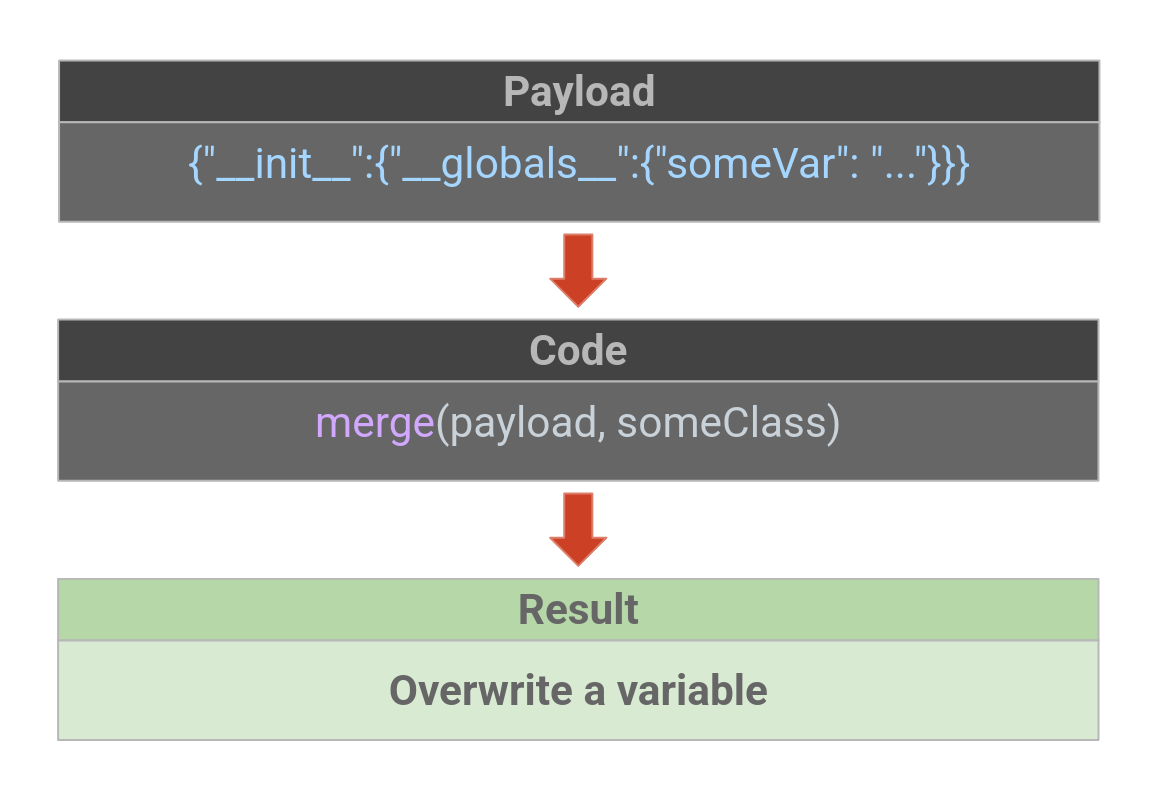
Now that you know how you can use this techniques to your advantage, you can test your practical skills in the official lab below.